Odd thing: when I go to Whitehouse.gov and allow Flash, the site complains about my privacy settings.
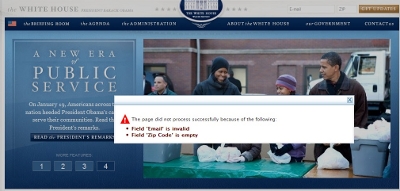
Click for a larger image.
The error message says,
The page did not process successfully because of the following:
• Field 'Email' is invalid
• Field 'Zip Code' is empty
Second odd thing: I wanted the full text of the order postponing trials at Guantanamo, the one that caused the following motion to be filed in Guantanamo,
In order to permit the newly inaugurated President and his administration time to review the military commission process, generally, and the cases currently pending before the military commissions, specifically, the Secretary of Defense has, by order of the President directed the chief prosecutor to seek continuances of 120 days in all pending case.
The Secretary of the Defense issued his order to the Chief Prosecutor in order to provide the administration sufficient time to conduct a review of detainees currently held at Guantanamo Bay, Cuba to evaluate the cases of detainees not approved for release or transfer to determine whether prosecution may be warranted for any offenses those detainees may have committed, and to determine which forum best suits any future prosecution.
But when I search for “Guantanamo” at whitehouse.gov I get … nothing.
