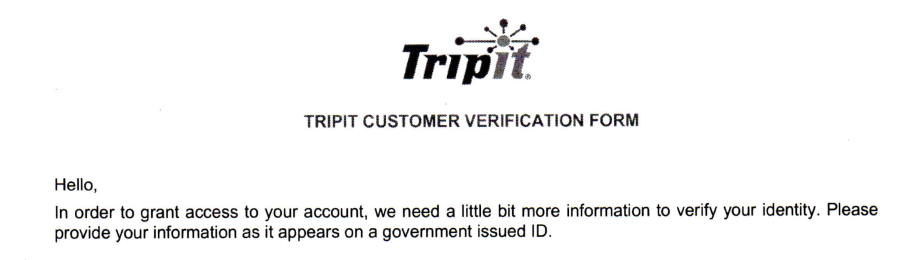
Admittedly, its been a long time since I tried to use Tripit, the handy travel itinerary planner site. Today I noticed that my Tripit widget on my phone wanted me to re-login, so I tried to do that. Didn’t work.
OK, maybe I have the wrong password, let’s try the web version. Password manager confirms I have the right password, but still no dice:
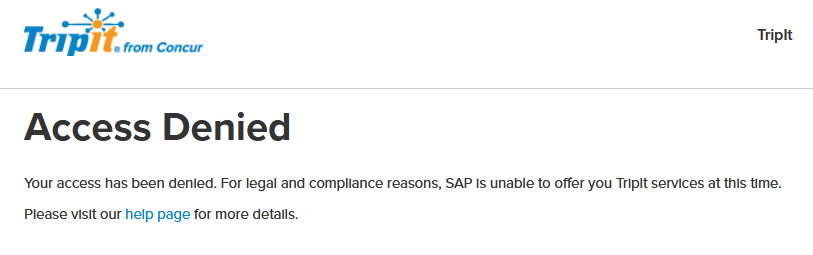
OK, maybe the link to the help page will explain this?

Well, that’s odd.
Seems to me there are four possibilities:
- Tripit is having a bad day.
- For some weird reason (unlikely to be my VPN since that’s set to a domestic location), Tripit wrongly thinks I’m located abroad or on a watch list / Treasury sanctions list.
- Tripit has decided that Florida is a foreign country they will no longer serve.
- I am on a watch list or a Treasury asset control list. (Would be news to me.)
I’m betting on #2, but we’ll see. I opened a ticket with Tripit, and will report back if I hear anything. Then again, if they think I’m on some list, maybe they don’t even answer help requests.
Other possibilities?
 Thanks to the kindness of others, I now have my own Wiki page. (Strangely, MiamiLaw doesn’t routinely make them for any of its faculty, which I suppose is consistent with our ahem, rather quiet media strategy.)
Thanks to the kindness of others, I now have my own Wiki page. (Strangely, MiamiLaw doesn’t routinely make them for any of its faculty, which I suppose is consistent with our ahem, rather quiet media strategy.)
 At least, I thought so….
At least, I thought so…. I sent in my form, and that seems to have done the trick.
I sent in my form, and that seems to have done the trick.